LitCTF复现
LitCTF复现
世界上最棒的程序员
直接扔进ida,F5反编译后直接看到flag
ez_XOR
1 | strcpy(Str2, "E`}J]OrQF[V8zV:hzpV}fVF[t"); |
XOR:
1 | size_t __cdecl XOR(char *Str, char a2) |
很简单的异或操作,直接把str2亦或9即可
enbase64
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
进入base64
1 | signed int __cdecl base64(char *Source, char *Str, char *a3) |
basechange函数是要换表,根据换表步骤换表即可,但是这里我用python写出来的代码换表不成功,c语言就行
1 |
|
换表后,表为:gJ1BRjQie/FIWhEslq7GxbnL26M4+HXUtcpmVTKaydOP38of5v90ZSwrkYzCAuND
直接进入basecheck函数拿到加密的字符串即可解密
snake
pyc文件直接拿去反编,发现缺少magic number,补齐这个文件的magic number,这个文件版本为3.7,magic number为 42 0D 0D 0A,2.7版本:03 F3 0D 0A
3.5和3.6版本:33 0D 0D 0A
补齐之后直接反编
1 | uncompyle6.exe xxx.pyc > xxx.py |
然后直接在代码中找到flag的数据,直接转换为字符即可
For Aiur
先用pyinstxtractor解包
1 | python pyinstxtractor.py xxx.exe |
得到pyc文件,本地的uncomple6没有反编译出,找了个在线网站编译,得到的py文件里唯一有用的信息就是调用了ch包里的check函数,在前面解的包里的PYZ-00.pyz_extracted文件夹中有ch.pyc文件,反编译,
1 | enc = [ |
直接根据代码写脚本即可
1 |
|
程序和人能跑一个就行
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
这是一个RC4加密,这里的Buf1是假的flag,因为无论如何if语句都会执行,去找真的flag的数据,在sub_475190处设下断点,然后运行,F8把这个函数跳过,往后面找,就可以找到真正的flag数据
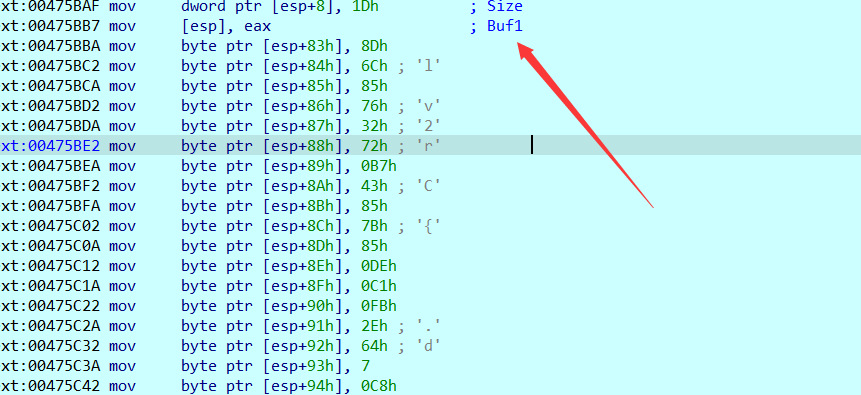
前面提到了密钥为litctf,直接写出脚本即可
1 | from Crypto.Cipher import ARC4 |
debase64
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
进入 sub_401520
1 | int __cdecl sub_401520(_BYTE *a1, int a2) |
一个类似base64的算法,将输入的20个字符分为4组每组分别反序做base64运算,这里字符会与v4作比较,直接在sub_401520处设个断点进入就能看到v4的值了
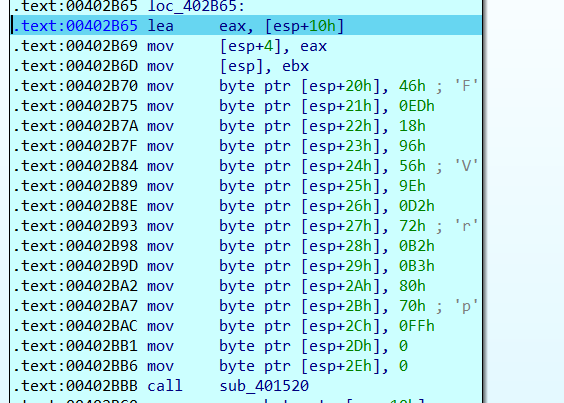
但是拿到的字符会有一位不知道,因为题目给了最后的md5值,直接爆破就好,脚本如下
1 | import base64 |
总结
知道了ARC4加密方式的处理,知道了magic number。